NC Encrypt

The NC Protect document security solution provides enterprises with the ability to find, classify and secure unstructured data across Microsoft applications in cloud, on-premises, and hybrid environments. Out-of-the-box, NC Protect’s policy-based encryption allows documents in M365 applications to be secured automatically based on user attributes, context, and file sensitivity, protecting data no matter where it is stored or travels.
Pairing NC Protect with the NC Encrypt add-on module offers dynamic encryption capabilities and Hold Your Own Key (HYOK) for M365. It’s the perfect solution for organizations that prefer to maintain control of their encryption keys in the Cloud to maintain data sovereignty.
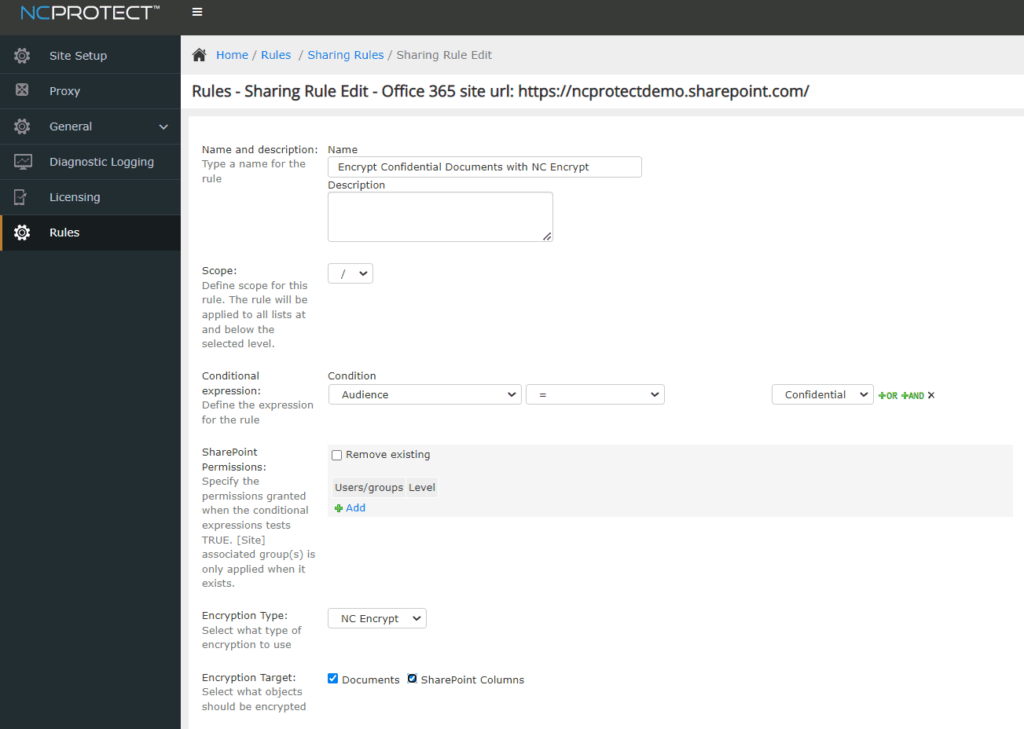
Use NC Encrypt’s dynamically created keys or supply and manage your own keys. NC Encrypt has the option to integrate with third-party key management platforms using Thales CipherTrust Manager, which provides connectivity to Hardware Secure Module (HSM). Linking CipherTrust Manager to NC Encrypt provides an innovative solution that allows you to manage your encryption key processes independently in CipherTrust Manager while managing your dynamic encryption and access controls in NC Protect.
NC Encrypt’s agentless design means there’s no administrative overhead. There are no encryption keys or passwords that need to be shared with end users or endpoints. No software to be installed and maintained or endpoint policies to update.
NC Protect allows you to take control of your keys in M365 to meet security and compliance objectives.
NC PROTECT
NC Protect for File Shares
NC Protect provides real-time data loss protection for Windows file sharing systems by monitoring and reviewing data against defined policies.
Learn moreNC Protect for Microsoft 365
NC Protect offers customers a comprehensive security solution focused on data-centric protection for Microsoft 365 applications and file sharing on the Windows platform.
Learn moreKey Management System (KMS)
Complior KMS (Key Management System) manages the organization's encryption keys with CipherTrust Manager from Thales Group for optimal security and management.
Learn more

